How to remove a Trojans Horse Virus
Removing a Trojan Horse
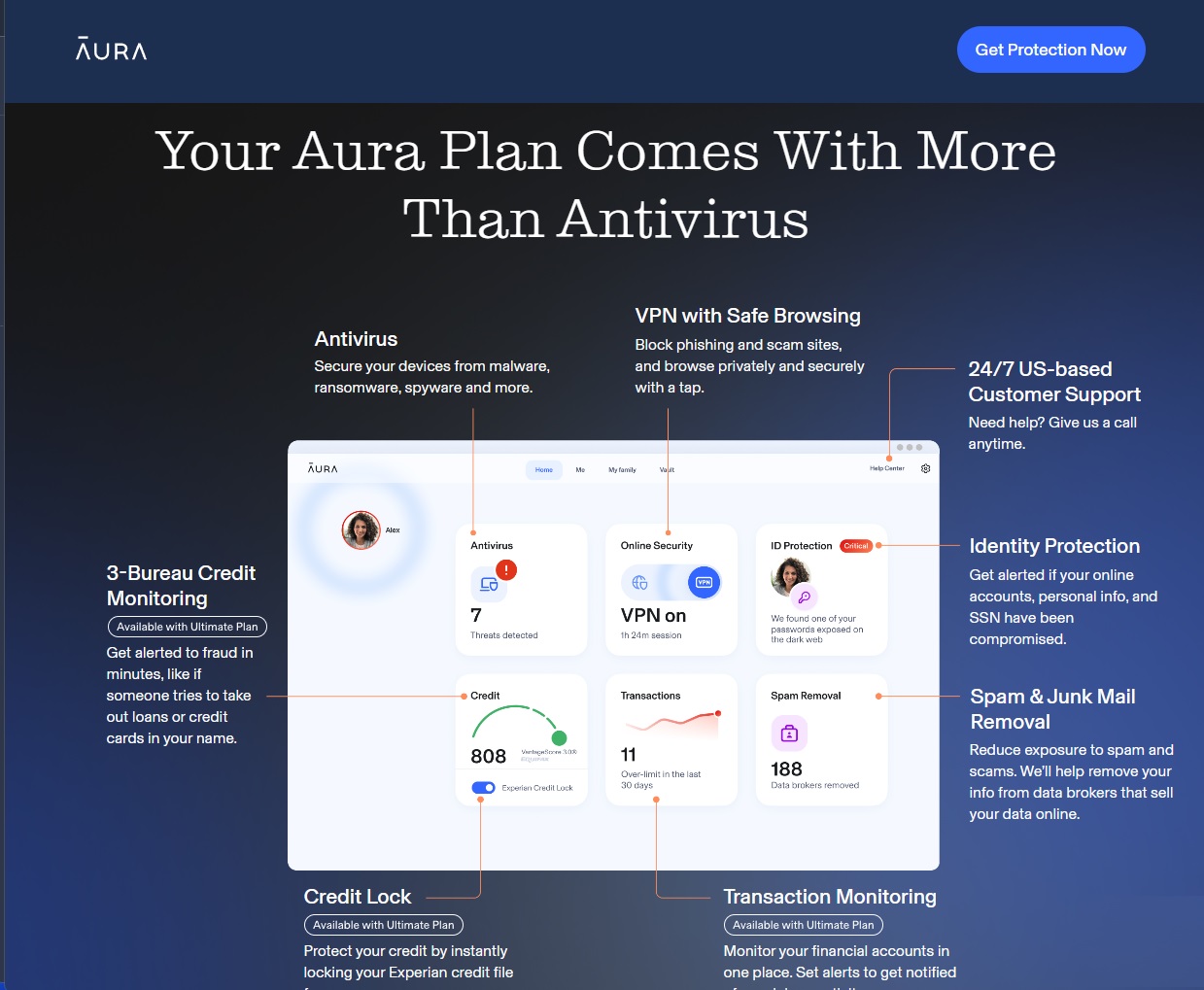
Removing a trojan can be simple if you have any good antivirus system installed. Perform a system scan to source the virus and then delete the virus. It can be this simple. If nothing is picked up...
What is a Trojan Horse?
What is a Trojan Horse?
The Trojan Horse virus takes its name from the Giant wooden horse that was used to trick the defenders of troy into sneaking soldiers into their city to ultimately win a war. How the modern day tr...